Jeremiah Johnson is a retired Green Beret of the United States Army Special Forces (Airborne) and a graduate of the U.S. Army’s SERE school (Survival Evasion Resistance Escape).
“…There is no place where espionage is not used.”
( Sun-Tzu, “The Art of War,” 13:14, The Employment of Secret Agents)
Good Day to you, SHTF readers! We’ve just concluded several pieces on home defense. At the behest of Sixpack and Talon 1776 who requested pieces on clandestine movement techniques and offensive operations (repectively), I present this article for a precursor. The best foundation for offensive operations in general is rooted in sound intelligence, and sound intelligence is not only found: it is made.
Look at this site. Those of you who read my last article (Defensive Techniques 102) saw what I mentioned toward the close: to use this site. The exchange of information and ideas is critical to development of comprehensive strategy. Read the comments section; really read them. You have the basis for a network of reliable information and intelligence outside of the norm. Such is Rule Number 1: Discount no piece of true information as useless. The reason? Even if the data is not usable at the moment, it may yet tie into subsequent intelligence.
The minds are there, in the comments section: fine minds, from a diverse group of thinkers, veterans, and people from all walks of life. You must become an analyst, weighing the information you find and deciding on whether to use it to your advantage in whatever situation you may face. You must sift through the articles and the comments and use the information: store it, categorize it, and remember it. Comes a day, and a day is coming where all we have written here – writers and commentators alike – will eventually be declared “illegal” by the Statists pushing toward their goal: totalitarian control in its entirety.
The government controls the mainstream media, either directly (through bureaucratic edicts and regulations, such as the FCC’s “fairness” doctrine), or indirectly by those nabobs and oligarchs who vend their falsehoods (lies and obfuscations of fact mislabeled as “news”) to garner favor with the ruler and follow his slant. Sites such as these are the last bastions of true freedom of the press and peaceable assembly (albeit electronically).
Lord Acton wrote, “Power corrupts, and absolute power corrupts absolutely,” and this holds true in the normal scheme of things; however, it truly referred to the press of a state fawning up to the ruler and abandoning its sacred (yes, sacred) duty to present factual and objective journalism to the citizenry. SHTF is one of those bastions. Gather intelligence, sift the relevant data, and use it to exchange ideas and be “facilitators of information” to one another.
Now what about your locale? How do you develop good intelligence locally? Who can you trust, and who is reliable on such matters? In short, your intelligence sources will be broken down into two categories: Allies and Assets. The first is fairly self-explanatory; the second needs to be examined in depth. Both are critical in the formulation of your pre and post-SHTF-activities.
Allies are just that: your network of family, friends, neighbors, and co-workers whom you trust and have established relationships with through the years. Allies will (as with all people) have different levels of reliability as varied as the human race. You must coordinate your efforts with them and “triage” them on some sort of scale of reliability and trustworthiness. Some may have good intentions but tend to talk too much. Others may say few words but also take few actions. They are allies because of the established relationship. They may be able to help you on some things but are limited on others. Allies can tell you the “Basic Big Six,” the who, what, when, where, how, and why of things happening in your locale.
These allies can be developed to provide you with specific information. An example is such: Jerry the crane operator tells you that he saw a fleet of 10 Chinese cargo ships unloading at Dundalk Marine Terminal in Baltimore and the most he has ever seen in his 30 years there is 2 ships. If you had spoken with him before, you might have been able to prep him (develop him) with information you wanted: What were the company names on the ships? Were the ships registered? Were the containers? What were the numbers for each? Did you notice what was being transported and were there variances between what you saw and what was listed?
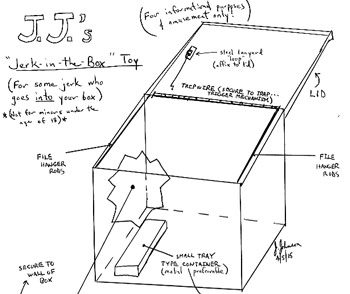
These are the types of details you need your allies to obtain for you. The prime challenge you face is to gauge the accuracy and reliability of the ally and to task him accordingly to obtain information you need. A file on each ally will be necessary in your long-term operations; you can code it and protect their actual identity. I recommend keeping the files in hanging files format, alphabetized, in a lockable metal file box with a gallon of gasoline and a lighter or matches next to it. In the event of compromise, take it outside and burn the files in its very own burn container. Or you can rig it up to turn into a “toy,” as I have outlined for you in my diagram entitled, “JJ’s Jerk-in-the-Box” toy, operated with a jar of brake fluid and a tray of powdered HTH (Calcium Hypochlorite), the two in tandem to enable a “vanishing act” of your files at a temperature greater than 4,000ºF.
(Click here for full-sized diagram)
Now for the other intelligence category: the assets. IGA’s (Intelligence Gathering Assets) each require a file. The acronym I wish to show you is CARE-FW:
C – Characteristics: Gender, height, weight, age, marital status, occupation, religion, habits, and general character traits
A – Access: The asset has access to what fields/sources of information you are:
- Currently seeking, or 2. May need in future operations [Is this asset a government employee? An executive in the defense contracting industry?]
R – Reliability: This can be assessed initially (as an estimate), and then later gauged in accordance with performance. [Is the information accurate? Is it provided in a timely manner, in the manner specified?]
E – Encouragement: What is the asset’s motivation to gather intelligence for you? Six reasons for encouragement are as such: money, a cause, revenge, drama, social interest, “romantic”/sexual interest.
Rule: 1 or more of these six reasons motivates all IGA’s, singly or in combination.
F – Factors: Miscellaneous factors that come into play that will weigh whether or not the intelligence is reliable and that determine how the asset can best be employed.
W – “Winds of Change”: all of these facts and data can change in an instant!
Rule: Today’s asset for you can be tomorrow’s informer against you!
You will need to exercise the greatest of caution regarding any asset you use or develop for whatever reason. Remember, readers, never expose your plans, resources, and network to an asset, and keep exposure to a minimum for an ally. This basic outline will help you to start and formulate your own plan. The aforementioned outline is by no means exhaustive and you can tailor it to your needs.
Rule: Never allow assets to meet one another or know of one another. Never.
Rule: An asset may become an ally after years of scrutiny; however, an asset is not an ally.
When an asset is meeting you to provide you with information, tell him to meet you at one point, a specific location (point A), giving him a 5-minute “window” to meet you. Have the location watched by an ally. You and your ally need to sync watches. Within that 5-minute window (when the asset is stationary), switch the meeting  point to a location with only one route to reach it 2-3 miles distant (point B). Your ally (communicate with Motorola’s) then needs to tail the asset and watch to see if the asset is followed along the route to point B. If so, pull your ally out and cut all communication to the (now former) asset.
point to a location with only one route to reach it 2-3 miles distant (point B). Your ally (communicate with Motorola’s) then needs to tail the asset and watch to see if the asset is followed along the route to point B. If so, pull your ally out and cut all communication to the (now former) asset.
Never drive your vehicle to within 1 mile of the meeting location with an asset. Reach the location by a circuitous route, and return to the vehicle in like manner but by a different route. Note down everything about the asset in your file: the date, time, what he wore, what he ate or drank, and all of the conversation. With time, bits and pieces will begin to unfold and your notes will provide you with a reliable snapshot photo of his character and usefulness. These are adverse times we are living in, and we must be wise beyond our wits in order to defeat the forces arrayed against us, against freedom-loving, Constitutional American patriots.
This article is for informational purposes only and does not give any consent or direction, explicit or implied, by SHTF’s writers or staff, to act upon the information in any manner that may violate local, state, or federal laws.
Develop your allies and assets. Remember the files! If something happens to you, you can potentially establish contacts for the use of your family and closest allies. These are adverse times, but if you stay strong in your mind and focused, you can plan accordingly and develop a good local network of intelligence sources. Remember, adversity doesn’t build character: it reveals it. Let the adversity of the times we are in be a guide in helping you to assess your sources of intelligence.
“Subtle and insubstantial, the expert leaves no trace; divinely mysterious, he is inaudible. Thus he is master of his enemy’s fate.”
(Sun Tzu, “The Art of War,” 6:9, Weaknesses & Strengths)
Readers, fight the good fight, develop expertise, and help one another every day. We can stand firm if we believe in one another and ourselves. I believe in you guys and gals and I learn from you, as well. Have a great day!
Source: shtfplan.com
Other useful resources:
Survive The End Days (Biggest Cover Up Of Our President)
Survival MD (Best Post SHTF Medical Survival Guide Ever)
Blackout USA (EMP survival and preparedness guide)
Backyard Innovator (All Year Round Source Of Fresh Meat,Vegetables And Clean Drinking Water)
Conquering the coming collapse (Financial advice and preparedness )
Liberty Generator (Easy DIY to build your own off-grid free energy device)
Backyard Liberty (Easy and cheap DIY Aquaponic system to grow your organic and living food bank)
Bullet Proof Home (A Prepper’s Guide in Safeguarding a Home )
Family Self Defense (Best Self Defense Strategies For You And Your Family)
Sold Out After Crisis (Best 37 Items To Hoard For A Long Term Crisis)
Jeremiah Johnson is the Nom de plume of a retired Green Beret of the United States Army Special Forces (Airborne). Mr. Johnson is also a Gunsmith, a Certified Master Herbalist, a Montana Master Food Preserver, and a graduate of the U.S. Army’s SERE school (Survival Evasion Resistance Escape). He lives in a cabin in the mountains of Western Montana with his wife and three cats. You can follow Jeremiah’s regular writings at SHTFplan.com.